By Matheus V. X. Ferreira, Danny Yuxing Huang, Tithi Chattopadhyay, Nick Feamster, and S. Matthew Weinberg
Recent years have seen a proliferation of “smart-home” or IoT devices, many of which are known to contain security vulnerabilities that have been exploited to launch high-profile attacks and disrupt Internet-wide services such as Twitter and Reddit.
The sellers (e.g., manufacturers) and buyers (e.g., consumers) of such devices could improve their security, but there is little incentive to do so. For the sellers, implementing security features on IoT devices, such as using encryption or having no default passwords, could introduce extra engineering cost. Similarly, security practices, such as regularly updating the firmware or using complex and difficult-to-remember passwords, may be a costly endeavor for many buyers.
As a result, sellers and buyers security practices are less than optimal, and this ends up increasing vulnerabilities that ultimately impact other buyers. In other words, their actions cause a negative externality to other buyers. This scenario where individuals act according to their own self-interest on detrimental to the common good is referred to as the tragedy of the commons.
One approach to incentivize agents to adopt optimal practices is through external regulations. In this blog post, we discuss two potential approaches that a regulator may adopt in the case of IoT security:
- Regulating the seller – requiring minimum security standards on sellers of IoT devices;
- Regulating the buyer – and/or encouraging IoT device buyers to adopt security practices through rewards (e.g., ISP discounts for buyers without signs of malicious network traffic) or penalties (e.g., fines for buyers of devices that engaged in DDoS attacks).
The goal of this hypothetical regulator is to minimize the negative externality due to compromised devices while maximizing the profitability of device manufacturers. We show that in some cases if buyers are rewarded for security practices (or penalized for the lack thereof), sellers can potentially earn higher profits if they implement extra security features on their devices.
Challenges in regulation
The hypothetical regulator’s ability to achieve the goal of minimizing negative externality depends on whether buyers can secure their devices more efficiently than sellers.
If, for instance, buyers regularly update their devices’ firmware or set strong passwords, then regulating the sellers alone can be costly — i.e., inefficient. On the other hand, rewarding buyers for security practices (or penalizing them for the lack thereof) can still be inefficient if there is little buyers can do to improve security, or if they cannot distinguish good vs bad security practices.
These challenges lead us to explore the impact the efficiency of buyers in improving their security has on regulatory effectiveness.
Modeling the efficiency of buyers’ security practices
A stochastic model captures the uncertainty of the efficiency of the buyer’s security practices when incentivized through regulation. A buyer has low efficiency when improving their effort towards security has a low impact in actually reducing security risks than if the same effort came from sellers. On the other hand, a buyer has high efficiency if improving their effort towards higher security translates in high improvements in security.
As an example, consider the buyer’s efficiency in a system where users (i.e., buyers) log into a website using passwords. Let’s first make two assumptions:
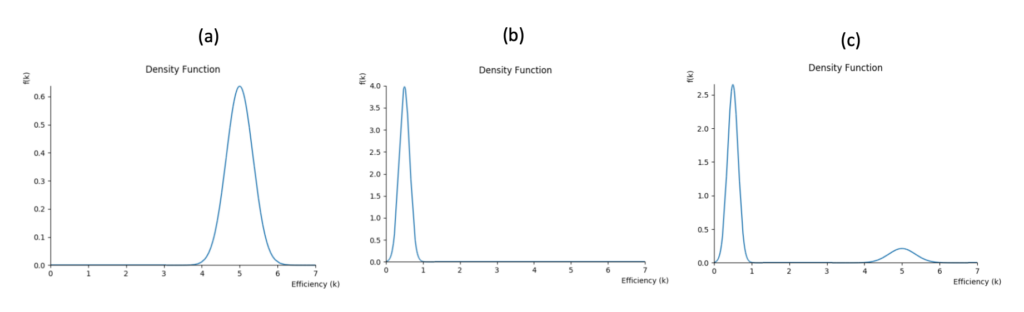
- We first assume that the website is secure. The probability of a user’s account being compromised depends on, for instance, how strong the password is. A weak password or a reused password is likely correlated with a high chance of the account being stolen; on the other hand, a strong, random password is correlated with the opposite. We say that the users/buyers are highly efficient in providing security with respect to the website operator (i.e., seller); in this case, efficiency > 1. Figure 1-a shows an example of the distribution of the buyers’ efficiency.
- We next assume that the website is not secure — e.g., running outdated server software. The probability of a buyer’s account being compromised depends less on password strength, for instance, but rather more on how insecure the website server is; in this case, efficiency < 1. Figure 1-b shows an example of the distribution of the buyers’ efficiency.
In reality, Assumptions (1) and (2) rarely exist in isolation but rather coexist in various degrees. We show an example of such in Figure 1-c.
The same model can be used to study scenarios where the actions of different agents cause externalities to common goods such as clean air.
Regulatory policies in a market of polluting cars often focus on regulating the production of vehicles (i.e., sellers). Once a car is purchased, there is little the buyer can do to lower pollution besides regular maintenance of the vehicle. In this case, the buyer’s efficiency would resemble Figure 1-b.
In the other extreme, in government (i.e., sellers) auctions of oil exploration licenses, firms (i.e., buyers) are regulated and fined for potential environmental impacts. When comparing the efficiency of the government vs. the efficiency of firms, firms are in a better position in adopting better practices and controlling the environmental impacts of their activities. The firms’ efficiency would resemble Figure 1-a.
Regulatory Impact on Manufacturer Profit
Another consideration for any regulator is the impact these regulations have on the profitability of a manufacturer.
Any regulation will directly (through higher production cost) or indirectly impact the sellers’ profit. By creating economic incentives for buyers to adopt better practices through fines (or taxes), we indirectly affect the prices a buyer is willing to pay for a product.
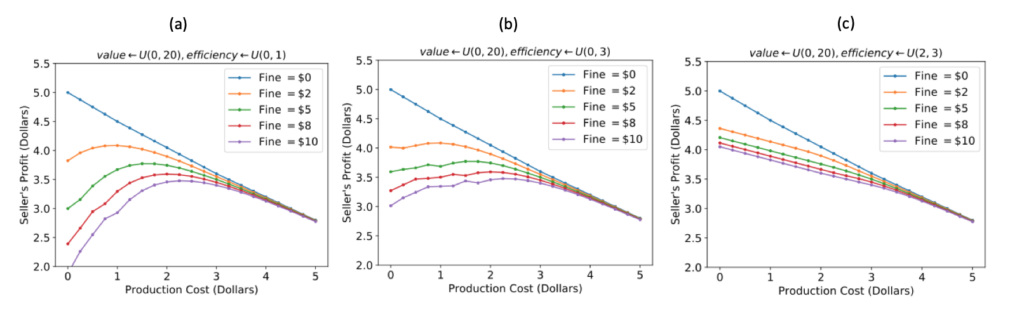
In Figure 2, we plot the maximum profit a seller can acquire in expectation from a population of buyers such that:
- buyer’s value for the IoT device is drawn uniformly between $0 and $20; efficiency is uniform [0,1], [0,3] and [2, 3];
- a regulator imposes on buyers a fine ranging from $0 to $10 and/or impose on sellers minimum production cost ranging from $0 to $5 (e.g., for investing in extra security/safety features).
If buyers have low efficiency (Figure 2-a) and they are liable for the externalities caused by their devices, regulating the sellers can, in fact, increase the manufacturer’s profit since the regulation reduces the chance buyers are compromised. As buyers become more efficient (Figure 2-b and then 2-c), regulating the sellers can only lower profit since they prefer to provide security themselves.
Selecting the Best Regulation
To select the optimal regulatory strategy when constrained by minimum profit impact on sellers, we must understand the distribution of efficiency of buyers.
We show that in homogeneous markets where buyer’s ability to follow security practices is always high or always low (Figure 1-a and 1-b) — the optimal regulatory policy would be to regulate only the buyers or the sellers.
In arbitrary markets where buyer’s ability to follow security practices can have high variance (Figure 1-c), by contrast, we show that while the optimal policy may require regulating both buyers and sellers, there is always an approximately optimal policy which regulates just one. In other words, although an efficient regulation might be required to regulate both buyers and sellers, considering policies that either only creates incentives for buyers or only regulate the seller can approximate the optimal policy that potentially intervenes on both buyers and sellers.
In practice, it is challenging to completely infer all the features that can affect the efficiency of buyers — that is, precisely measure efficiency distributions Figure 1-a to 1-c. Our theoretical results provide a tool for security researchers to infer an approximately optimal regulation from an inaccurate model of the efficiency distribution.
By estimating that most of the population that purchase a device is highly efficient, we have shown that regulating only the buyer is approximately optimal. On the other hand, by estimating that the population that purchases a device is highly inefficient, regulating only the seller approximates the optimal regulation.
At the end of the day, by better understanding the efficiency of buyer’s security practices, we will be in a better position to make a decision about regulatory strategies for different information technology markets such as for the market of IoT devices without the need for complex regulation.
For more details, the full paper can be accessed at https://arxiv.org/abs/1902.10008 which was presented at The Web Conference 2019.


Leave a Reply